You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
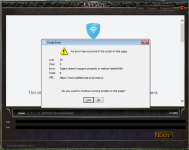
Bug Report script popup when launching mir?
- Thread starter prasko
- Start date
Gritt
Active Member
Your antivirus has updated and blocked a component of MiR
Basically you anti virus has not allowed the connection Java script that is part of the authentication to the login service
Simple fix allow your MiR update exe in you antivirus as a known good application
For extra safety just in case any 1 being malicious
Re download entire mir to a new directory eg mir safe from the official book mark
Once that is done
Remove all the . Exe files from your existing nir folder
Then copy the newly downloaded. Exe like launcher mirpatcher to the original folder
Then allow these . Exe in your antivirus
I am on the road so no acces to PC atm so going on my memory of file names
Basically you anti virus has not allowed the connection Java script that is part of the authentication to the login service
Simple fix allow your MiR update exe in you antivirus as a known good application
For extra safety just in case any 1 being malicious
Re download entire mir to a new directory eg mir safe from the official book mark
Once that is done
Remove all the . Exe files from your existing nir folder
Then copy the newly downloaded. Exe like launcher mirpatcher to the original folder
Then allow these . Exe in your antivirus
I am on the road so no acces to PC atm so going on my memory of file names
Last edited:
You're right about the important bit, that it's because of antivirus, but not completely right about the reason or what to do about it.Your antivirus has updated and blocked a component of MiR
Basically you anti virus has not allowed the connection Java script that is part of the authentication to the login service
Simple fix allow your MiR update exe in you antivirus as a known good application
For extra safety just in case any 1 being malicious
Re download entire mir to a new directory eg mir safe from the official book mark
Once that is done
Remove all the . Exe files from your existing nir folder
Then copy the newly downloaded. Exe like launcher mirpatcher to the original folder
Then allow these . Exe in your antivirus
I am on the road so no acces to PC atm so going on my memory of file names
Read on if you're really REALLY bored and want far too much technical detail.
It's nothing to do with any authentication. It's just while the autopatcher is running it displays some images about the update. Ever wonder how it gets the new images for the update before it's even downloaded the patch?
The application runs what's called a 'webview' which you can think of as a cut down version of Microsoft Edge, where everything is removed except the ability to actually see a webpage. And that runs inside the app. So it loads that up and 'visits' a particular url where GM can post new images etc., so they will always show the most up to date ones.
In this particular case, the url that shows those images has triggered something in your antivirus which has redirected you to the address you see in the popup (safebrowse.io). That url is probably just going to show you a message explaining that it's been triggered. But whoever runs safebrowse has likely created it with the thought that it would only run in a regular browser, and not tested it properly in a webview, which runs cut down versions of the engine, and has less properties available to it. That is what's then triggered the popup, which is just a javascript error on the safebrowse site.
I wouldn't be concerned about this at all. But GM may have interest to see your antivirus logs to he can find out what on his page has triggered it, it's quite common for Mir-related things to find themselves on blacklists that such antivirus things apply blindly without much care for nuance. If that's happened then GM will be able to request his url to be removed from the list.
Likewise, safebrowse might be interested to see the javascript error, as it could help them in improving their testing methods and remind them to include webviews
Gritt
Active Member
Zade , is in the right ball park , Like I said was on the road so not had access to PC to write a detaialed explanation , I have seen this a few times when changing from 1 anti virus to another also when is had certain malware scrappers running on my sandbox.You're right about the important bit, that it's because of antivirus, but not completely right about the reason or what to do about it.
Read on if you're really REALLY bored and want far too much technical detail.
It's nothing to do with any authentication. It's just while the autopatcher is running it displays some images about the update. Ever wonder how it gets the new images for the update before it's even downloaded the patch?
The application runs what's called a 'webview' which you can think of as a cut down version of Microsoft Edge, where everything is removed except the ability to actually see a webpage. And that runs inside the app. So it loads that up and 'visits' a particular url where GM can post new images etc., so they will always show the most up to date ones.
In this particular case, the url that shows those images has triggered something in your antivirus which has redirected you to the address you see in the popup (safebrowse.io). That url is probably just going to show you a message explaining that it's been triggered. But whoever runs safebrowse has likely created it with the thought that it would only run in a regular browser, and not tested it properly in a webview, which runs cut down versions of the engine, and has less properties available to it. That is what's then triggered the popup, which is just a javascript error on the safebrowse site.
I wouldn't be concerned about this at all. But GM may have interest to see your antivirus logs to he can find out what on his page has triggered it, it's quite common for Mir-related things to find themselves on blacklists that such antivirus things apply blindly without much care for nuance. If that's happened then GM will be able to request his url to be removed from the list.
Likewise, safebrowse might be interested to see the javascript error, as it could help them in improving their testing methods and remind them to include webviews
Hope you get it fixed bud